Apple has spent years reinforcing macOS with new security features to make it tougher for malware to break in. But a newly discovered vulnerability broke through most of macOS’ newer security protections with a double-click of a malicious app, a feat not meant to be allowed under Apple’s watch.
Worse, evidence shows a notorious family of Mac malware has already been exploiting this vulnerability for months before it was subsequently patched by Apple this week.
Over the years, Macs have adapted to catch the most common types of malware by putting technical obstacles in their way. macOS flags potentially malicious apps masquerading as documents that have been downloaded from the internet. And if macOS hasn’t reviewed the app — a process Apple calls notarization — or if it doesn’t recognize its developer, the app won’t be allowed to run without user intervention.
But security researcher Cedric Owens said the bug he found in mid-March bypasses those checks and allows a malicious app to run.
Owens told TechCrunch that the bug allowed him to build a potentially malicious app to look like a harmless document, which when opened bypasses macOS’ built-in defenses when opened.
“All the user would need to do is double click — and no macOS prompts or warnings are generated,” he told TechCrunch. Owens built a proof-of-concept app disguised as a harmless document that exploits the bug to launch the Calculator app, a way of demonstrating that the bug works without dropping malware. But a malicious attacker could exploit this vulnerability to remotely access a user’s sensitive data simply by tricking a victim into opening a spoofed document, he explained.
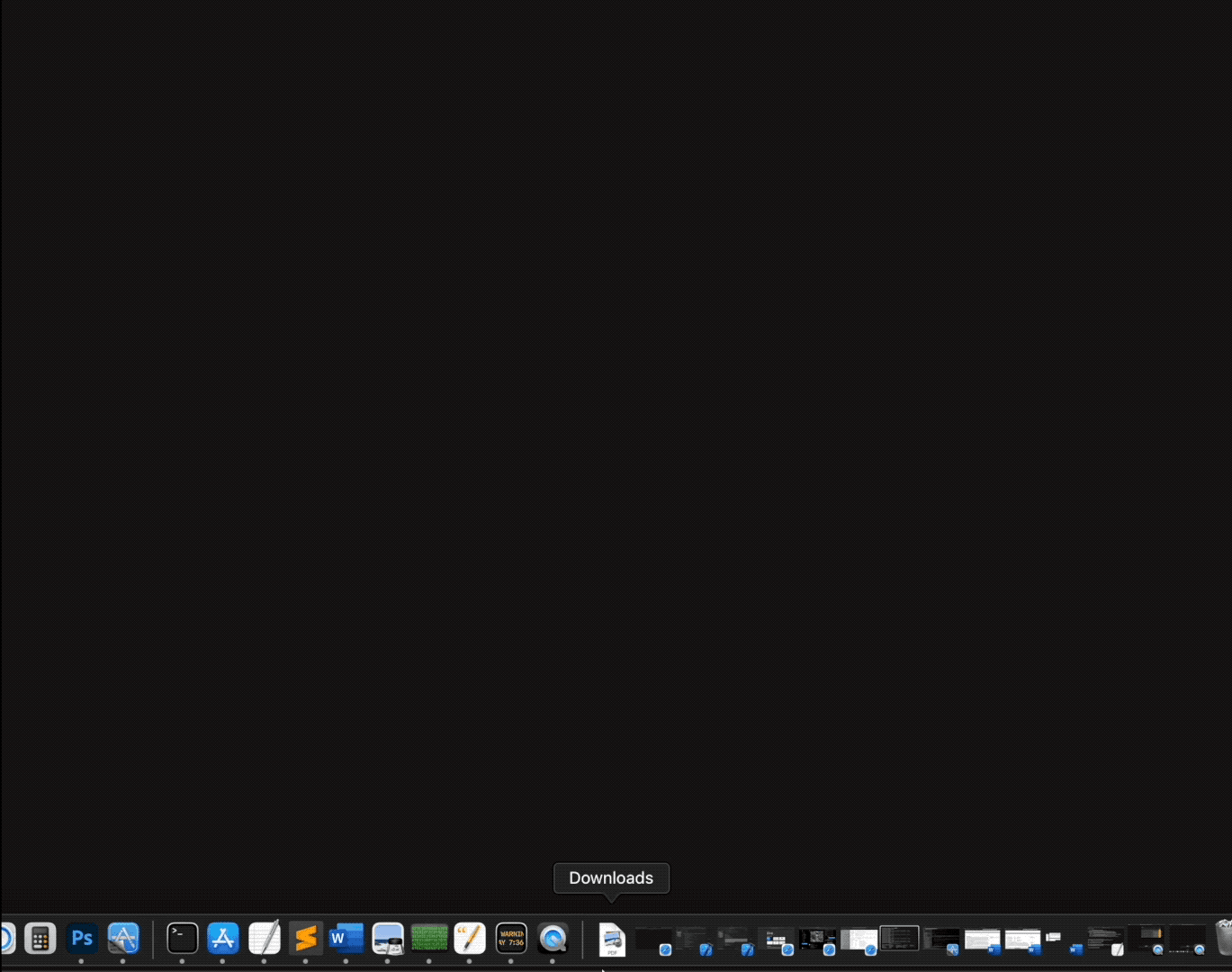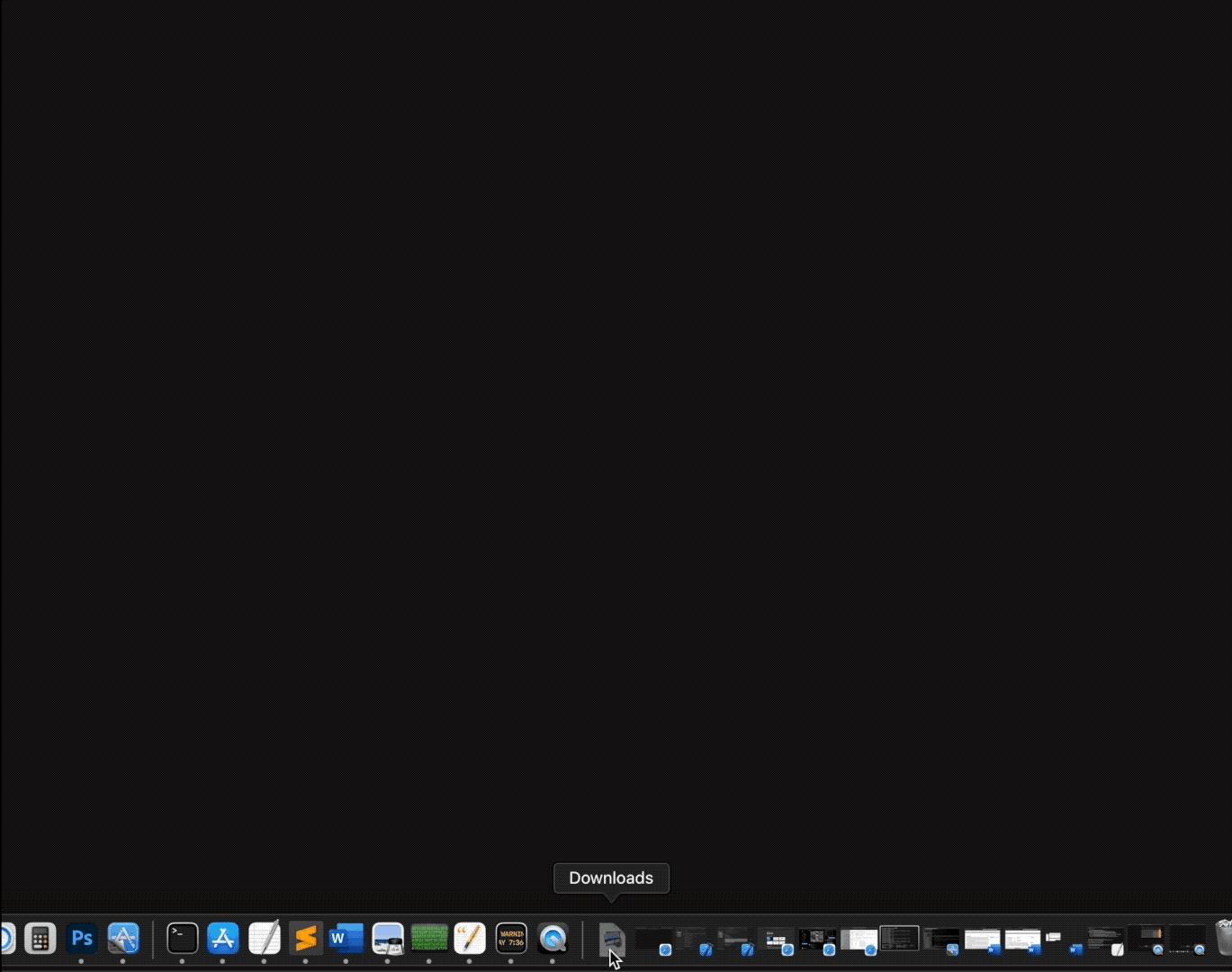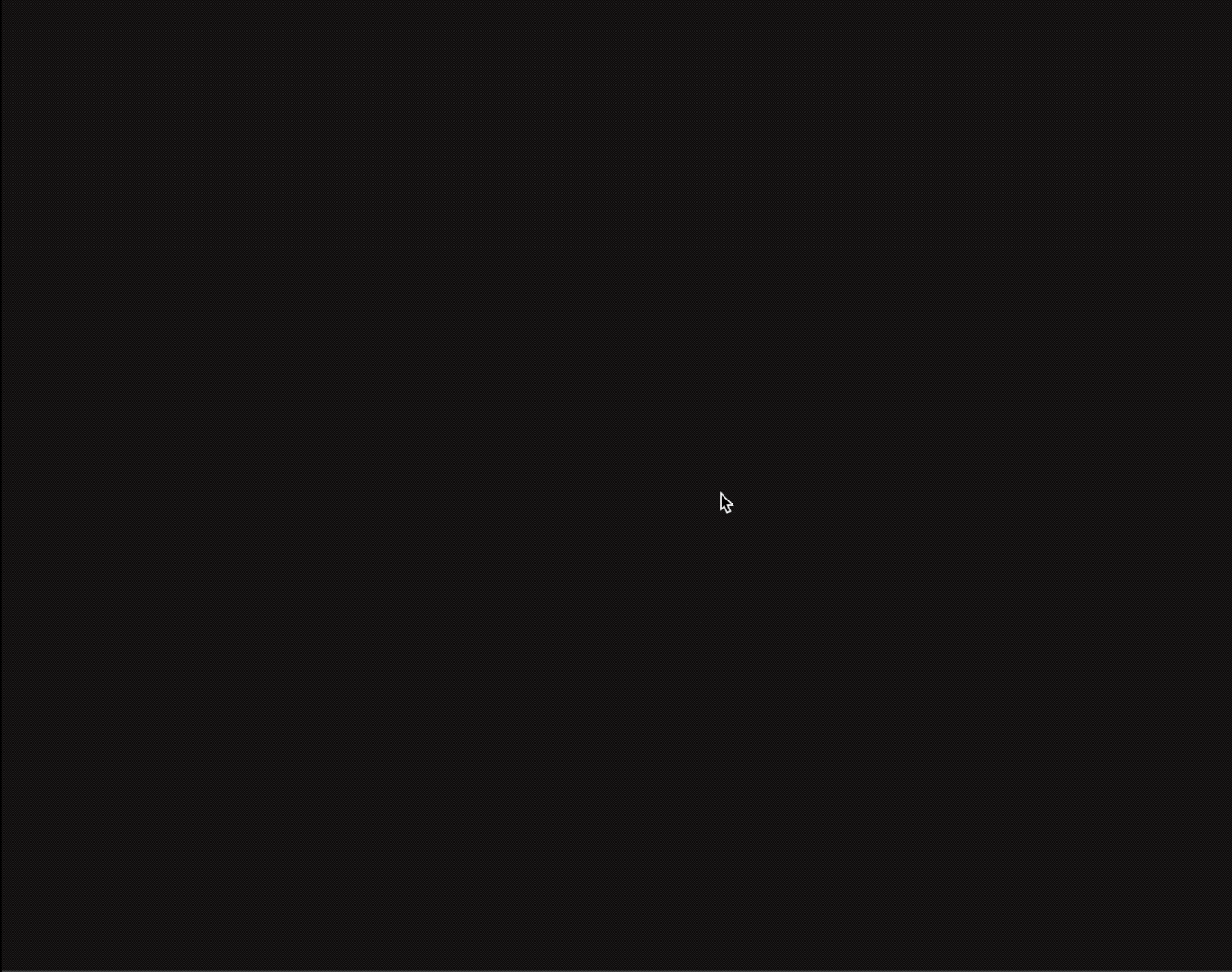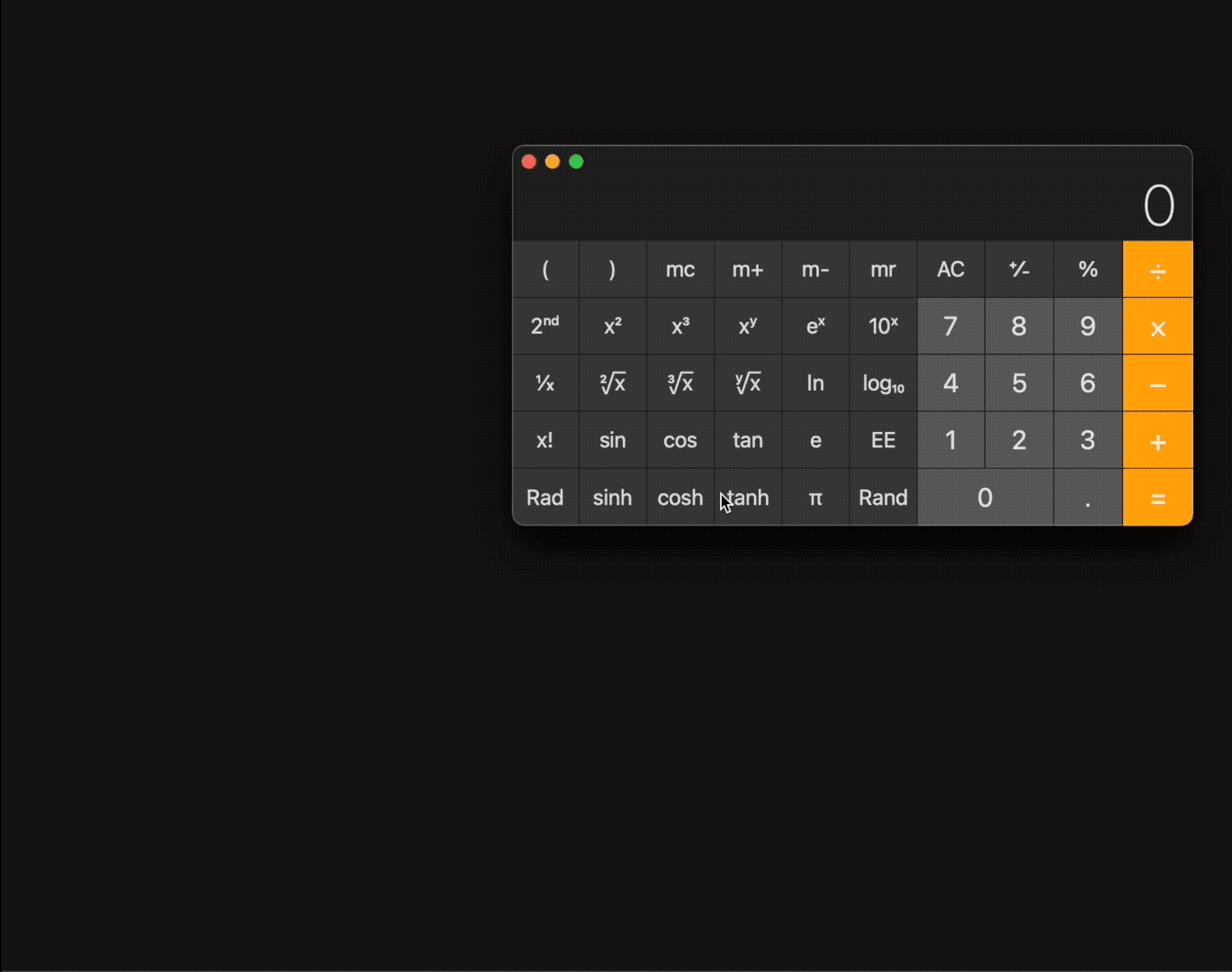
The proof-of-concept app disguised as a harmless document running on an unpatched macOS machine. (Image: supplied)
Fearing the potential for attackers to abuse this vulnerability, Owens reported the bug to Apple.
Apple told TechCrunch it fixed the bug in macOS 11.3. Apple also patched earlier macOS versions to prevent abuse, and pushed out updated rules to XProtect, macOS’ in-built anti-malware engine, to block malware from exploiting the vulnerability.
Owens asked Mac security researcher Patrick Wardle to investigate how — and why — the bug works. In a technical blog post today, Wardle explained that the vulnerability triggers due to a logic bug in macOS’ underlying code. The bug meant that macOS was misclassifying certain app bundles and skipping security checks, allowing Owens’ proof-of-concept app to run unimpeded.
In simple terms, macOS apps aren’t a single file but a bundle of different files that the app needs to work, including a property list file that tells the application where the files it depends on are located. But Owens found that taking out this property file and building the bundle with a particular structure could trick macOS into opening the bundle — and running the code inside — without triggering any warnings.
Wardle described the bug as rendering macOS’ security features as “wholly moot.” He confirmed that Apple’s security updates have fixed the bug. “The update will now result in the correct classification of applications as bundles and ensure that untrusted, unnotarized applications will (yet again) be blocked, and thus the user protected,” he told TechCrunch.
With knowledge of how the bug works, Wardle asked Mac security company Jamf to see if there was any evidence that the bug had been exploited prior to Owens’ discovery. Jamf detections lead Jaron Bradley confirmed that a sample of the Shlayer malware family exploiting the bug was captured in early January, several months prior to Owens’ discovery. Jamf also published a technical blog post about the malware.
“The malware we uncovered using this technique is an updated version of Shlayer, a family of malware that was first discovered in 2018. Shlayer is known to be one of the most abundant pieces of malware on macOS so we’ve developed a variety of detections for its many variants, and we closely track its evolution,” Bradley told TechCrunch. “One of our detections alerted us to this new variant, and upon closer inspection we discovered its use of this bypass to allow it to be installed without an end user prompt. Further analysis leads us to believe that the developers of the malware discovered the zero-day and adjusted their malware to use it, in early 2021.”
Shlayer is an adware that intercepts encrypted web traffic — including HTTPS-enabled sites — and injects its own ads, making fraudulent ad money for the operators.
“It’s often installed by tricking users into downloading fake application installers or updaters,” said Bradley. “The version of Shlayer that uses this technique does so to evade built-in malware scanning, and to launch without additional ‘Are you sure’ prompts to the user,” he said.
“The most interesting thing about this variant is that the author has taken an old version of it and modified it slightly in order to bypass security features on macOS,” said Bradley.
Wardle has also published a Python script that will help users detect any past exploitation.
It’s not the first time Shlayer has evaded macOS’ defenses. Last year, Wardle working with security researcher Peter Dantini found a sample of Shlayer that had been accidentally notarized by Apple, a process where developers submit their apps to Apple for security checks so the apps can run on millions of Macs unhindered.
[ad_2]
Source link


